
Microsoft has shared more details about the new Windows 11 administrator protection security feature, which is available in preview and uses Windows Hello authentication prompts to block access to critical system resources.
First introduced last month in a preview build for Windows 11 Insiders in the Canary Channel, admin protection is designed to « protect free floating admin rights for administrator users allowing them to still perform all admin functions with just-in-time admin privileges. »
More to the point, once enabled on a device, this feature will ensure that those logged into the system only have standard user permissions and will be asked to authenticate via Windows Hello using a PIN or biometric method when trying to change the registry or install new apps.
These extra authentication prompts should be more challenging to circumvent than the Window User Account Control (UAC) security feature so that they can prevent malware and attackers from accessing such critical resources and compromise the system.
« Windows creates a temporary isolated admin token to get the job done. This temporary token is immediately destroyed once the task is complete, ensuring that admin privileges do not persist, » said David Weston, the company’s Vice President for Enterprise and OS Security, at Microsoft Ignite.
« Administrator protection helps ensure that users, and not malware, remain in control of system resources. It will also be disruptive to attackers as they no longer have automatic, direct access to the kernel or other critical system security without specific Windows Hello authorization. »
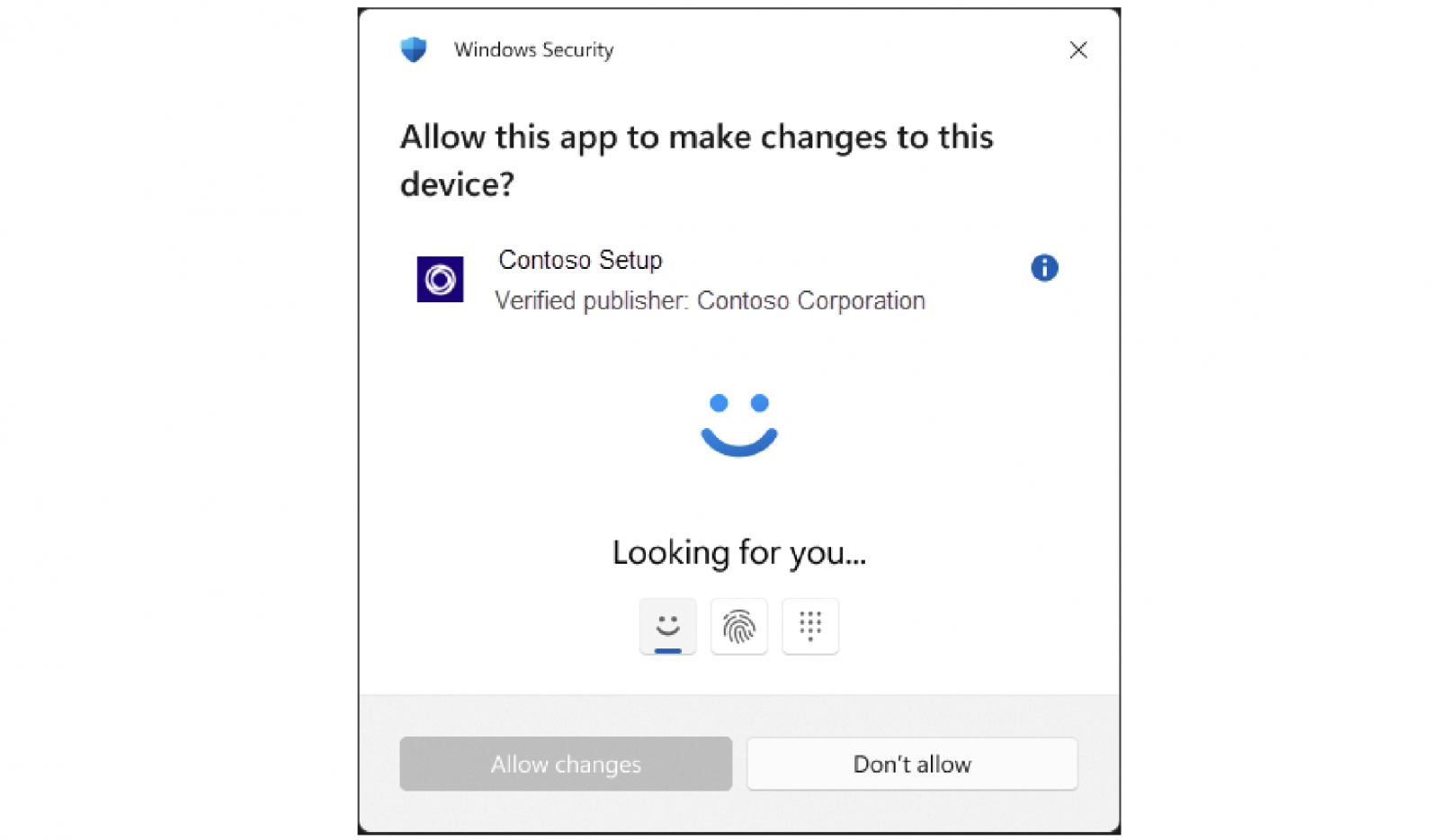
As the Windows Insider Team shared in October, when the feature was first introduced, admin protection is off by default and must be enabled via group policy.
Windows Hello is also used for authentication to block access to files stored in the Desktop, Documents, and Pictures folders with the help of Personal Data Encryption, a feature introduced with Windows 11 22H2 that encrypts the data so the device administrator can’t even access it before authenticating.
Admins can now also enable Smart App Control and App Control for Business policies to prevent users from downloading, installing, and running malicious apps and drivers.
« Many attacks occur due to users downloading unsafe or unsigned apps and drivers. This eliminates attacks like malicious attachments or social engineered malware, » Weston added.
« IT admins can simply select the ‘signed and reputable policy’ template in the app control wizard. This enables millions of verified apps to run regardless of the deployment location. »
Plus de détails sur l’article original.


